Next planned improvments are:
-) Reopen the tree after Save/Delete (currently it gets collapsed after this Action)
-) Handle the output of pass (e.g. Info that the password was copied to clipboard, Display of error messages)
Nice 
Eventually I will try out the OTP plugin.
The thing is that I usually use gopass on all my pc. But since it’s technically compatible with pass things works 
Testing OTP Plugin:
If you create a new entry in my GUI you just need to enter the “OTP Secret” as password and change the type dropdown.
The collapsing tree after save/delete is now fixed in V0.4
New features in V0.5
-) Added Progress Bar to visualize when the password is available in clipboard
-) Fixed action “New” when no existing element is selected
I was successfully running this on my Pinephone running Mobian during the summer, but it appears to be broken now? I haven’t dug deep into the reasons why but I’m suspecting some python version shenanigans…
@Cc281080 i can’t wait to make use of this lil’ program on my L5 
for CLI nerds > https://lbry.tv/@Luke:7/pass-a-password-manager-two-factor:6
Can you please open a terminal and send me the ouput of the following two commands:
python --version
pass --version
And also please check if the following command gives you the list of your stored entries.
But there is no need do send the list to me:
pass
Sure!
Of course this is over Mobian which is now mostly based on Bullseye, it’s not PureOS, but here goes:
$ pass --version
============================================
= pass: the standard unix password manager =
= =
= v1.7.3 =
= =
= Jason A. Donenfeld =
= Jason@zx2c4.com =
= =
= http://www.passwordstore.org/ =
============================================
$ python --version
-bash: python: command not found
$ python3 --version
Python 3.8.6
$ python3 ./pass-mgr-compact
File "./pass-mgr-compact", line 30
new_time = progressbar.get_fraction()*progress_max_time*progress_bps
^
TabError: inconsistent use of tabs and spaces in indentation
Now for some installation errors of the .deb:
$ sudo dpkg -i ./pass-mgr-compact_0.5.deb
[sudo] password for mobian:
Selecting previously unselected package pass-mgr-compact.
(Reading database ... 81538 files and directories currently installed.)
Preparing to unpack ./pass-mgr-compact_0.5.deb ...
Unpacking pass-mgr-compact (0.5) ...
dpkg: dependency problems prevent configuration of pass-mgr-compact:
pass-mgr-compact depends on python-gi; however:
Package python-gi is not installed.
dpkg: error processing package pass-mgr-compact (--install):
dependency problems - leaving unconfigured
Processing triggers for desktop-file-utils (0.26-1) ...
Processing triggers for mime-support (3.64) ...
Errors were encountered while processing:
pass-mgr-compact
$ sudo apt install python-gi
Reading package lists... Done
Building dependency tree
Reading state information... Done
Package python-gi is not available, but is referred to by another package.
This may mean that the package is missing, has been obsoleted, or
is only available from another source
E: Package 'python-gi' has no installation candidate
$ sudo apt install python3-gi
Reading package lists... Done
Building dependency tree
Reading state information... Done
python3-gi is already the newest version (3.38.0-1+b1).
python3-gi set to manually installed.K, I will try it on Debian Bullseye and see if I need to make a new version for python3 or if I can make an universal version.
New features in V0.6
-) Switched to python3 incl. fixes for compatibility
The version 0.6 should work for you.
I tested it under Debian Buster and Bullseye.
0.6 worked perfectly, and I can actually copy the passwords this time after reading the README and installing both wl-clipboard and wl-clipboard-x11
thanks for the quick turnaround!
New Features in V1.0
-) Rounded “Last modified” to only one digit.
-) Successfully tested on a pyhsical Librem5 (incl. OTP & TOMB)
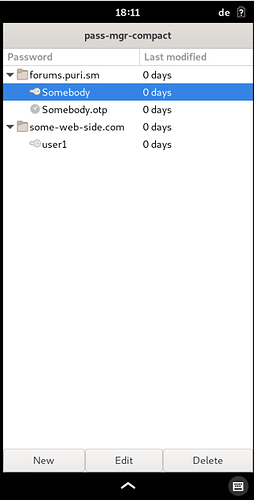
Screen Shots please!!!
TOTP-Code / password is copied to clipboard using a double click.
I am currently experimenting with making the entries bigger.
Folders are generated when “/” are included in the name.
New Features in V1.0
-) Optimized Scalling for Librem5
-) Switched from os.system/os.popen to subprocess
Just installed it for the first time on my desktop - thanks a lot!
A thing I’m really missing is a search field. My list is several screens long.
Otherwise looks great and I’ll try to run it on the Librem5 soon.
I will look into the search field.
I also thought in the past about it.
I’m just trying pass with tomb on my Librem5:
purism@pureos:~$ pass open -v
. pass Opening the password tomb /home/purism/.password.tomb using the key /home/purism/.password.tomb.key
. tomb . Commanded to open tomb /home/purism/.password.tomb
. tomb . An active swap partition is detected...
. tomb [W] This poses a security risk.
. tomb [W] You can deactivate all swap partitions using the command:
. tomb [W] swapoff -a
. tomb [W] [#163] I may not detect plain swaps on an encrypted volume.
. tomb [W] But if you want to proceed like this, use the -f (force) flag.
. tomb [E] Operation aborted.
[x] Error : Unable to open the password tomb.
purism@pureos:~$ swapon -s
Filename Type Size Used Priority
/dev/zram0 partition 1530876 0 100
purism@pureos:~$ sudo zramswap status
NAME ALGORITHM DISKSIZE DATA COMPR TOTAL STREAMS MOUNTPOINT
/dev/zram0 lzo-rle 1,5G 4K 80B 12K 4 [SWAP]
I didn’t dive deep into the subject and I’m willing to accept that an unencrypted swap partition poses a risk to the tomb.
How does this compare to a zram device as swap on a system that is used by one local user? Is there a similar attack vector as for an unencrypted swap written to disk?
Edit: Decided to put it into an issue for tomb.
Edit: Modified the tomb script to recognize zramswap. Pull request is accepted.
If you run into the issue and you want to make sure that you do not accidentality --force other warnings to be ignored now or at some point in the future, use the version from the repo.
If you have swap in RAM then it’ll disappear as soon as you cut the power. If its on disk, it’ll remain until it gets overwritten. I guess the vector would be the same while the computer is on, but nobody could steal your powered-off computer and read the disk to find the swap if it was in RAM.