Shortly after 9/11, I remember doing Quality Control on OSINT data entries and one of them said a gas station was blown up by bad guys. Then after a quick purview I determined that the website it was collected from was doing a ROLE PLAYING GAME, and I called for deletion of the entry. That’s one of the problems of raw intel when it meets analysis.
Or people using airliners to fell tall buildings and kill people? Clearly, all flight controls should be fingerprint and retina scan activated. No, that’s too complicated… just ban airliners altogether.
Edit: Well that’s lame. I put “sarcasm” markup on part of the above and the forum removed in when rendered (I can still see it when I edit). It seems more harsh without the humorous markup. Apologies.
Ah! That’s it. You see it as a privilege to be granted (lent), I see it as a right to be protected. Not much middle ground there, but I promise to buy the beer if we ever meet in person.
…and provided to you within 24 hours of the the disclosure.
Governments may have legitimate reasons to not want terrorist and criminal groups to know that their activities are being watched. Maybe a better solution is to say that all decisions are published after 5 years, but the government can apply to the citizens’ board to delay publishing decisions for specific ongoing cases for another 5 years.
If they haven’t caught them after 10 years of secret surveillance, then they probably aren’t going to catch them.
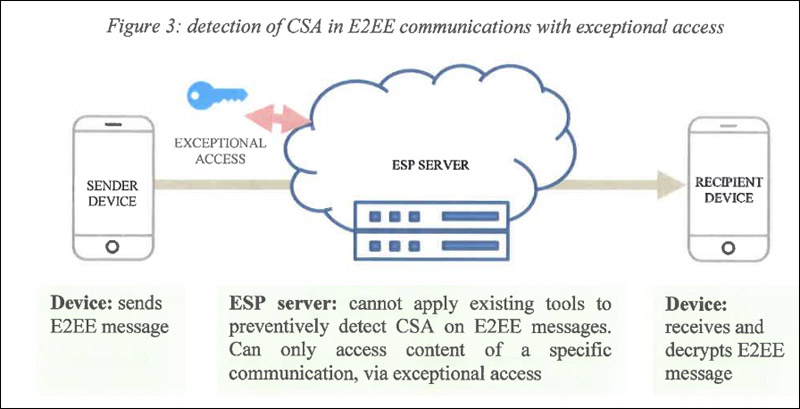
There are a couple of interesting things in that draft declaration from the EU council.
It clearly states, in a couple of places, that strong encryption and lawful powers of the police etc must be provided at the same time - but it then goes on to talk about a balance. To me, that is a contradiction - either you provide both at the same time, or you trade one for the other in a balance. I cynically assume there is no real intention to do both, but to make it a discussion about how to compromise encryption.
Law enforcement and <…> must be able to access data in a lawful and targeted manner, in full respect of fundamental rights and data protection regime, while upholding cybersecurity.
(Emphasis mine)
It is of a paramount importance that this matter is handled in a coordinated way at EU level <…> to define and establish
innovative approaches <…>
<…>should be developed in close consultation with service providers and the relevant authorities, while there should be no single prescribed technical solution to provide access to the encrypted data.
(Emphasis mine)
Since it is a draft, we still have time to influence the outcome. We need to tell our representatives that broken encryption can’t uphold cybersecurity and that technical “solutions” that have been refuted again and again over the years are in no way innovative.
Old joke:
Street preacher on Wall Street: “Take heed evil is growing!”
Passerby: “Where can I get a franchise?”
yeah, maybe, if your highest forgiving authority is a corrupt-wordly-organization …
you say that as if there aren’t any ‘gov.’ ‘officials’ who are there for MORE than 30 years ![]()
unless you have a non-changing-benevolent-omnipotent-non-human-deity-that-can-not-be-influenced-by-any-other-beings in charge of global-cybersecurity then introducing ANY back-door is an EXTREMELY BAD idea.
that’s me at my most cynical point ![]()
is it a coincidence that this very authoritarian law comes a few days after you have won against Trump
I wouldn’t make any connection with the US. This is the EU going in a direction that other countries have already gone and other countries still will go in the future, of its own volition, not prompted by the US.
This proposal has not yet reached the status of “law” but authoritarian it is.
At the time of the Apple controversy over the San Bernardino case, a fellow named General Michael Hayden, who ran a little security firm called the CIA, stated that while a backdoor would be helpful, it wasn’t needed. In short order, he was proven correct.
Hayden’s position was that while strong encryption is used by criminals, mandated backdoors would be a bad idea.
Hayden basically refuted the FBI position at the time, saying there were other ways for law enforcement to get what they needed without actually breaking the encryption.
Hard not to connect dots with the U.S. here. Lindsey Graham and Diane Feinstein have been pushing for passage of the EARNIT act for a few years, to get big tech to backdoor their encryption, under the guise of protecting children from sexual predation. It really gained some traction in 2019.
The U.S. and EU have worked together to bag international child abuse rings. Sure seems reasonable to figure like mindedness on encryption growing out of those experiences.
The US is pushing for the US to go in the same direction.
Think of it as convergent evolution for technology (technological convergence). In other words, all governments perceive the same problem (to wit, they do not have total surveillance capability over all people in their country) and design approximately the same solution, because the solution is constrained by the same problem and external factors.
See also: US senate "Lawful Access Bill"
Yes, the EARNIT act is the Lawful Access bill.
The FBI has been spreading the gospel of backdooring encryption for a number of years, in it’s work with EU partners. I rather doubt this is sheer happenstance. Five eyes is more like fourteen, after all.
also look at each country’s military budgets … you’ll see the one that’s most invested in 
If the EU does try and ban encryption, nothing has been set in stone yet, then just use services based in non EU countries?
Also this “ban” so far seems specific to whatsapp & a few other apps. I’m sure there are other apps that can be used
If the government can decide if a backdoor is needed, than there is already a design problem with the service.