I thought that to. I have installed a a Wiki (ciwiki or so) on my PP. I thought this could become a generic personal knowledge database and possibly substitute some dedicated apps like note, recipe, bookmark apps etc… Now there is a service run on the phone with an open port and I don’t want it to be accessible to any network. Or at least not until I explicitly allow it. I will try if I can reach the service over the internet via cellular radio. I don’t know if cellular radio providers allow such connections. For other services it might be really interesting." Run your own webserver and email server ion the Librem 5 and offer them over mobile radio." 
That is not correct. The issue is that sudo (or su) often don’t pass your environment variables through cleanly. The solution is to specify the full path to the wayland display socket. Assuming the user who owns the display has UID 1000, the XDG_RUNTIME_DIR is /run/user/$UID, and you’re wanting to use Wayland Display 0, it turns into
sudo -i
WAYLAND_DISPLAY=/run/user/1000/wayland-0 $program-name
You can even use setfacl to let specific other users connect to a running wayland display (which is nice if you want to stick firefox under its own user account or similar).
Edit: Oops, wrong environment variable.
Oh of course you can make it work, it’s just a socket after all  But other than laziness, there’s also an issue of launching it via the desktop launcher that asks you for root password, but then fails to actually run the app because it doesn’t handle running it under Wayland at all.
But other than laziness, there’s also an issue of launching it via the desktop launcher that asks you for root password, but then fails to actually run the app because it doesn’t handle running it under Wayland at all.
Aye that’s fair enough. Who uses a desktop launcher though 
@dos could you please setup to block all incoming traffic as default? This is something i do everytime on my gufw to protect my devices from incoming packets
Agree, it’s not even about “privacy by default”, it’s just common sense.
Well on the subject of Privacy by default… You’re openssl library is in dire need of an update it’s version 1.1.1d instead of version 1.1.1i, I do believe and feel free to correct me if I am wrong that version 1.1.1g fixed the racoon attack vulnerability in the OpenSSL stack and trying to install libnettle or nettle just doesn’t seem to work as flawlessly as some might like, for example where is the gnutls package?? apt-get install gnutls - no such package. As for the firewall I gave up with trying to wrap my head around the GTK for gufw and just settled on firewalld and the only service that was running was cups as found by running - sudo lsof -i -P -n | grep LISTEN which was easy enough to disable and turn off.
We inherit security updates from Debian, where vulnerability fixes are backported into 1.1.1d. Amber/Buster is a stable distro so it generally doesn’t update its package versions unless absolutely necessary.
Ask Debian. I asked and it said apt install gnutls-bin 
Those who want to set up a firewall on their Librem 5 can do it just like they would on other hardware running PureOS.
As to the question of our setting up firewall rules by default, while people are free to add whatever security measures makes them feel safe, given that by default PureOS (like other desktop Linux distributions) don’t have any services listening on the network, firewall rules have limited utility/protection.
Arguably even on servers, local firewall rules only are useful in as much as they match and reinforce rules you have in place at the gateway, and only then if you deny by default, and have your network segregated enough to only allow specific hosts/subnets/etc. to talk to specific ports. Most modern security architectures have gone away from firewalls and the idea of perimeter security and more toward the “zero trust” model where you are less concerned with firewalls and network segmentation, because you don’t have an “inside” vs. an “outside”–you treat all networks as untrusted. Instead you focus on strong authentication between endpoints.
For desktops (and for the Librem 5) I’m more in favor of a “Little Snitch” type approach that would warn users about suspicious traffic (in particular outgoing traffic). We’ve looked into OpenSnitch in the past but sadly that project seems to be abandoned.
As I’ve mentioned in other threads, I am working on a hardening guide for the Librem 5 that will mention firewalls (briefly, again I’m not convinced on a desktop computer they are the best approach) among other things.
Is there, or can there be, in the future, a similar guide for the L14’s when they ship next month?
This is another great thing about the fact that it all runs PureOS. For the most part the hardening steps would be identical, except for when it comes to the cellular kill switch or lockdown mode or things very specific to the phone hardware. I was realizing this as I sat down to start writing the guide, that honestly most of the hardening steps I talk about in my book Linux Hardening in Hostile Networks, as it pertains to desktops and networks, would apply without rewriting anything.
Well I found fanny on my hard disk thanks to PureOS I get two (NOP) errors as the disk spins up looking to assign a MAC address to the HDD which of course fails because the HDD is encrypted - reasons to use full disk encryption part one. 
Will no doubt pull the HDD at some later date, cant be bothered to pull it ATM, Windows Vista was on this machine previously and belonged to a student who donated it graciously to me saying, I cant recover my photo’s can you - PureOS in live mode to the rescue, pics recovered and moved to removable USB.
When I asked if they wanted it back they said no, you can keep it. Result!
InsydeH20 Bios on a HP G60 with Altec Lansing speakers and a Core 2
I often find myself pondering the wonders of the FOSSIL filing system and find myself extrapolating the wording FOSSIL as “Free-Open-Source-Software” (IL) “Interface Link” and then find myself trying not to digress what it actually does or why RIO is not the default Window Manager.
Sometimes “ignorance is bliss!”
Funny how as GCC advances it leans more and more towards ISO/IEC 9899:2011 and C11 the much older standard and the newer standard (C18) goes flying out the Window.
I digress that Open Source is like an elaborate puzzle where you win a prize if you can figure out why SCO - the GTK and Webkit suck so badly!
As for OpenSSL> version
OpenSSL 1.1.1i 8 Dec 2020
I gave up with gnutls-bin when it came to configuring nettle or libnettle.
configure: error:
*** Libnettle 3.4.1 was not found.
I then compiled it by hand, installed it, ran gnutls configure and watched as it spat out the same recursive error over and over, despite installing both nettle 3.4.1 and 3.6
If in doubt re-install 32 bit openBSD and meditate on Linux being a burden on everybody!
Linus tout’s how Linux doesn’t break user space, sadly not in my experience, where you go to remove something as trivial as Chrome or Firefox and watch with horror as it removes half the desktop dependencies with it.
The reason C is classed as the desert island programming language is because nobody likes talking about magneto-optical disks and recording telephone calls, which most handset’s do by default and a few button clicks nowadays anyway.
Constitutionally fine to read other peoples emails if your the system administrator just as its constitutionally fine to record someone else’s telephone call if its juicy… c’est la vie
Other than the lockdown mode, there doesn’t appear to be a hardware kill switch for the GPS module in the L5. Even in lockdown mode, I am not sure how the GPS module could be connected directly to any hardware kill switches, given the way that the lockdown mode is enabled. With a combination of three hardware kill switches needing to be each individually set to power off before the GPS gets turned off also, that tells me that most likely a logic circuit and not simply depriving the GPS circuit of power by opening a manual switch, is what actually disables the GPS module. If the idea were to enable the GPS module only when all other hardware kill switches were set to power the other three hardware controlled modules at the same time also, I might think that a hardware kill switch method would be possible as long as all three modules require the same voltage level to power them. But we don’t want to power the GPS unit only when all three of the other kill switches power their respective modules also. That would be a three-input AND gate implemented through physical switches (not what we need). We want the opposite of that. The current implementation of lockdown mode requires a three-input OR gate with the existing three hardware kill switches as the inputs to the OR gate. Only when all three physical switches are open at the same time, is the GPS turned off in this case. How does Purism implement the disabling of the GPS module, given the actual electrical requirements needed to call that implementation of the GPS hardware kill switched? Do all three physical kill switches connect to the GPS module in parallel such that to kill the GPS unit, you need to disable power to all three of these modules to deprive any possible path of current to the GPS module? If so, all functions involved in any of the switching would be required to be powered at the same voltage levels to avoid voltage level contention amongst any of these modules. If resistors or even voltage regulators were used to create different voltage levels, there would be some power losses in the form of heat. Perhaps this is how it’s done. But it would be nice to betterstand this.
In any event, I understand that I can disable the GPS in software while leaving the radio active. Yes, the cell sites could track me through triangulation this way. But it is much less likely that anyone will be recording my every move throughout the day if I leave the GPS module turned off and if it really is off. As a matter of principal, I want to turn the GPS module on only when I need it and then immediately turn it off afterward. In your Android or Apple phone when you turn the GPS unit off, it looks like it is off and it is off to you. But Google and others still continue to use it to track you since it really isn’t turned off.
We had to make compromises given the constraints of three hardware switches. If you want to disable GPS outside of lockdown mode then you have to rely on disabling via software. At least in our case since everything is free software, you have better assurance (and better ability to audit) that a software switch actually does what it says it does.
The schematics have been published by Purism. May not be current for Evergreen but for your question they may answer it.
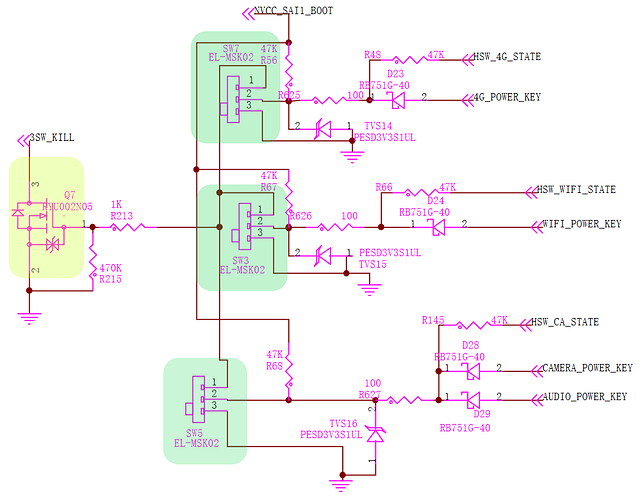
Published evergreen mainboard schematics is your friend. There you can see this:
Three hardware switches (SW7, SW3 and SW5, marked with green color) control a gate of the trasnistor Q7 (marked with yellow). They are connected to the gate of Q7 in parallel, so when all three are off, the signal 3SW_KILL is also off. (I’m not going into the details if OFF for the 3SW_KILL means 0V or 1.8V or something other, the point is, the signal is in one state when at least one switch is on, and in another state, when all three switches are off).
Now, from here the SW3_KILL signal goes out of the above picture, as controlling input signal to glorified op-amp U55, which separates it from other circuits, gives it some more power and normalizes it, so that it can be used as… controlling signal to voltage regulator U19, which powers the GNSS chip.
Hope this explains a little.
Thanks for responding with the schematic. I didn’t know where to find the schematic myself. The design looks good. Regardless of the VCC level to any of the other three modules, the Gate of Q7 will go high if power is supplied to any of the other three modules. It looks like the VCC in to each module is clamped at each respective module to an appropriate level and each individual module power input is grounded when the kill switch is in the off position. As Kyle mentioned, there were compromises given the constraints of the hardware switches. I am guessing that the current draw might be a little higher due to the switching circuit itself for each respective module, any time the phone is not in lockdown mode. But there aren’t a lot of good choices available when ideally, you want only nano-watt power consumption any time any circuit is active anywhere except for in a copper trace. Typically, that kind of performance has to be implemented in silicon. But without an SoC for everything, the biasing and clamping resistors typically cause some heat losses. The existing design appears to minimize those losses as much as is possible. But I would rather carry around a phone with a slightly bigger battery than to give up the hardware kill switches. Perhaps in a future design the design could implement a fourth switch for the GPS and hopefully find a way to do away with any resistors in the current path that powers a whole module.
Hi,
I am issues ufw on my Liberem 5.
command
# /usr/share/ufw/check-requirements
Returns:
RULE_INSERT failed (No such file or directory): rule in chain ufw-check-requirements
ERROR: could insert RETURN rule into ‘ufw-check-requirements’. Aborting
FAIL: check your kernel and that you have iptables >= 1.4.0
If I enable ufw, all inbound connections are block regardless of ufw rules created via ufw frontend.
Any thoughts?
It could be related to Debian buster’s (and therefore PureOS’s) transition to nftables from iptables starting with Buster:
https://wiki.debian.org/nftables
For the most part it’s backwards compatible but there are a few cases where scripts use advanced iptables flags that nftables doesn’t implement. I suspect your ufw script might be using one of those unsupported iptables arguments.
The link above also documents steps to revert back to iptables.
How did you install GUFW to your phone? I cant find it in the PureOS store and dont see any flatpaks with it?
Edit: sudo apt-get install -y gufw