First of all: well done; it looks like you’ve put a lot of work into this, and I’m sure you’ve put much more thought into it than I ever will.
Here are my thoughts. Take them with a grain of salt: I don’t speak with authority on this matter. I’ve only skim-read your paper and this thread, so I apologise if you’ve already expressed yourself on these points. Also, I’m not someone who’s likely to fund the project, so don’t spend too much time trying to appease me!
There’s a difference between the dissertation and this forum thread
It’s worth restating that your dissertation was about a device management protocol but this forum thread is about a more general purpose push notification protocol. You did say this, but I failed to register it on first reading.
I still don’t get what this is for
My overriding feeling is that I still don’t understand what you are proposing. Can you write some new user stories for the expanded project scope?
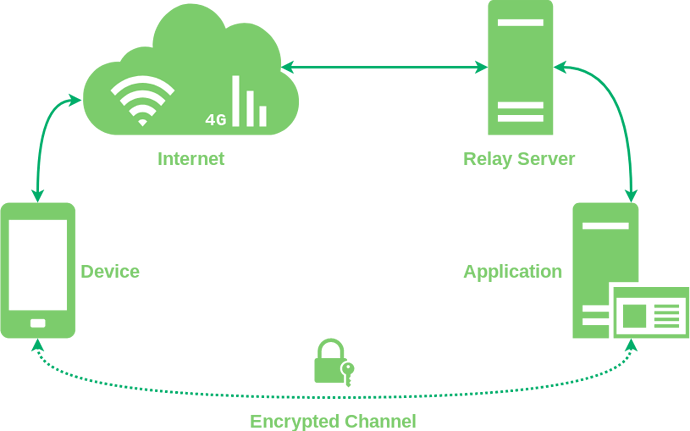
Who is expected to host the relay server?
Who is expected to run or host applications?
What’s an application?
It’s also not altogether clear to me what an “Application” is in your architecture. Having given it some thought, my assumption is that these could be:
- Phone management applications (for “find my phone” and “remote erase” kinds of use cases) - hosted on a server or running only on a ‘client’ device.
- Self-hosted or other cloud applications that run on a server and implement this protocol
- Adaptors that connect to cloud services and implement this protocol on behalf of those services (e.g. something that connects to your IMAP email account and issues push notifications when new mail arrives).
Is that correct?
I’m struggling not to confuse these applications with the applications that run on the mobile devices. It might be worth changing the naming convention to make it clearer what an application is. (Or what kind of application it is.)
The terms “client” and “server” are also ambiguous, because it depends on what perspective you are looking at the system from.
How does it interface with third party software and services?
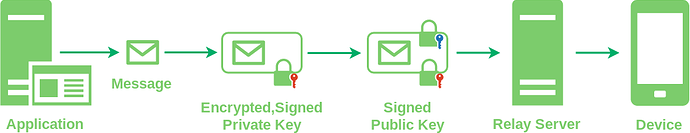
I assume there will be a library that implements the protocol, for use by applications? Or is there a daemon that implements the protocol and the applications communicate with that?
This question goes for both endpoints of the protocol: on the mobile device and on the other end (the application). How does one go about integrating push notifications into, say, an email app for the Librem 5 and into a corresponding email server?
Is NAT the real reason to have a relay server?
When I saw that your requirement for a relay server was exclusively derived from your requirement FR-2 (“The protocol must work when devices are behind a NAT and/or a firewall limiting incoming connections”) my first thought was that this seemed like something that should be an implementation detail rather than a core part of the protocol.
You acknowledged that there are other ways this could be implemented. I’d be inclined to define a relay abstraction that could represent either a relay server or some other means of relaying the messages. In practice, an alternative implementation could masquerade as a relay server even without a clean abstraction being defined, but that would be a bit of a hack.
It seems to me that the real reason to have a relay server might be to have a single point of contact for the mobile devices. Otherwise the devices would need to maintain connections to each individual application, or perhaps participate in a peer-to-peer network.
Won’t NAT be a solved problem where server applications are concerned?
It seems to me that many applications in this architecture would most sensibly be run on a server, in which case NAT may well be a solved problem, since those application servers would need to be publicly addressable regardless of whether they issue push notifications. Someone who can run a server without NAT being a problem can probably also run a relay server without NAT being a problem. Or does the push notification platform aim to replace other protocols that applications might use to communicate with the device, thereby allowing them to run from behind NAT?
Do some of the components of this system already exist?
@ruff made some points on this theme.
It struck me that the relay server is, in part, a message broker. Those already exist, and their protocols can be quite efficient with bandwidth and CPU cycles.