I really like this feature - no more USB tokens (forgotten at home when I need them 
OpenPGP allows encrypting emails, correct?
Is there more I can do with a OpenPGP card?
Really interesting to see that the Librem Key isn’t “pretty much” a smart card or just “recognized by the computer” as a smart card - it’s literally a smart card on a chip to enable interfacing over USB.
I use it with a smartcard for my Laptop (instead of a password) for:
-) Login / sudo
-) Authentication when doing SSH
-) Decrypting my LUKS Partition
-) Decrypting my password store
This is all protected with the smartcard. So only 3 tries to enter the correct smartcard pin.
Then the card ist locked and needs the admin pin (6 tries).
As some users stated - would have been interested to see also what can be done on a librem 5 with an OpenPGP or what is planned to be possible. (Like the things @Cc281080 writes)
… and how to do it?
Will I be able to move the card from the Librem Key to the phone, and then use the phone as a librem key? Meaning, connect the phone to a computer, and then have access to the the gpg-key on the computer?
I just started to test the integrated smartcard reader.
Downside for now:
As soon as I followed the description in the news my smartcard in my external card reader ist not used anymore.
I will program a small smartcard to test my How Tos with the internal smartcard reader.
I will Post the description if I have then verified in the Librem5.
Here are some of our plans for the future:
My description for SSH via SmartCard
Just tested it on my Librem5
On Client
vi .gnupg/gpg-agent.conf
enable-ssh-support
vi ~/.bashrc
export SSH_AUTH_SOCK=$(gpgconf --list-dirs agent-ssh-socket)
gpgconf --launch gpg-agent
reboot System
get SSH Key for Server authorized_keys
ssh-add -L
On Server paste SSH key
vi ~/.ssh/authorized_keys
Deactivate login on server via password (optional)
vi /etc/ssh/sshd_config
PasswordAuthentication no
No, if you remove the smart card from the Librem Key and put it in the Librem 5’s smart card reader, you won’t be able to connect the Librem 5 to your computer over USB-C and use it like a Librem Key.
Create Password store (with TOMB) on Laptop (tested on Debian)
su -
apt install pass-extension-tomb
adduser [Username] sudo
exit
Reboot to take effect
sudo swapoff -a
gpg --list-keys
pass tomb [gpg-id] -v -d
Workaround if error: cryptsetup luksFormat returned an error.
You need to remove the already generated .password.tomb
rm -rf .password.tomb*
Then you need to add “–type luks1” in tomb when the “cryptsetup” is called
sudo vi /usr/bin/tomb
/_cryptsetup(
sudo cryptsetup --type luks1 --key-file - ${@}
Copy the password store to the Librem5
apt install pass-extension-tomb
The following two files need to be copied to the librem5
~/.password.tomb
~/.password.tomb.key
Use a GUI for managing the passwords (optional)
On Matrix I read about another GUI for “pass” also writen in python but currently without support for pass-tomb.
I haven’t tested the other GUI and don’t have a link to it. But maybe some one can post it.
When I enter the pin the smartcard doesn’t ask for it anymore. An external card reader can be removed and reinserted into USB port.
Is there a way/command to do it with the integrated smartcard reader?
So that I would have to enter the pin again.
I think what you are seeing is a GPG session token being cached. I forget what the initial timeout is (a few minutes I believe) before GPG will prompt you again for the PIN. I’m sure it’s configurable though.
$ cat $GNUPGHOME/gpg-agent.conf
enable-ssh-support
max-cache-ttl 600
I see now (having the card in my L5) that the above value does not bring the card into locked state again. For the moment I only use killing the gpg-agent process.
I’m about to order my phone…Can someone please help me understand this?? Will I be able to put this in an Evergreen L5 for PGP stuff (signing, encrypting, etc)? I assume so, since its being offered as an L5 accessory? Just trying to determine if I want to get one with my order.
Yes. The OpenPGP card works nice with the L5. Here is my small how to set it up:
How to setup the OpenPGP card in the Purism L5 phone
guru@unixarea.de, October 2021
https://puri.sm/posts/openpgp-in-your-pocket/
(includes video about inserting the card)
https://source.puri.sm/angus.ainslie/ttxs-firmware/-/blob/purism/PURISM.md
install and get the software:
$ cd ~/guru
$ sudo apt install stm32flash git
$ git clone https://source.puri.sm/angus.ainslie/ttxs-firmware
$ cd ttxs-firmware
Upgrade the smart card reader firmware:
$ ./scripts/stm_reflash.sh
...
stm32flash 0.5
http://stm32flash.sourceforge.net/
Using Parser : Raw BINARY
Interface serial_posix: 57600 8E1
Version : 0x31
Option 1 : 0x00
Option 2 : 0x00
Device ID : 0x0435 (STM32L43xxx/44xxx)
- RAM : Up to 48KiB (12544b reserved by bootloader)
- Flash : Up to 256KiB (size first sector: 1x2048)
- Option RAM : 16b
- System RAM : 28KiB
Write to memory
Erasing memory
Wrote address 0x08002388 (100.00%) Done.
And set up the smart card:
$ ./scripts/smartcard_setup.sh
There have been issues, see also:
https://forums.puri.sm/t/openpgp-card-waiting-for-the-first-reader/15189
https://source.puri.sm/Librem5/OS-issues/-/issues/119
What helped was:
# stty -F /dev/ttymxc2 raw cstopb -parenb cs8 115200
# pcscd -f --debug
The startup of pcscd is to be configured here and start is via systemctl:
# vim /lib/systemd/system/pcscd.service
# systemctl status pcscd
# systemctl stop pcscd
# systemctl start pcscd
Setting up the card
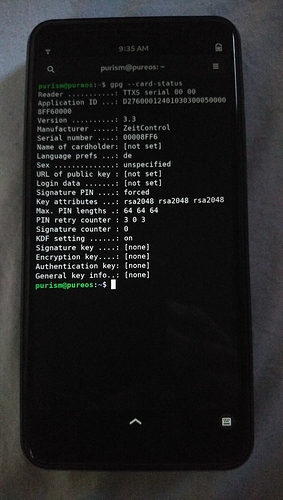
$ gpg --card-status
Reader ...........: TTXS serial 00 00
Application ID ...: D27600012401030400050000A6FE0000
Application type .: OpenPGP
Version ..........: 3.4
Manufacturer .....: ZeitControl
Serial number ....: 0000A6FE
Name of cardholder: [not set]
Language prefs ...: de
Salutation .......:
URL of public key : [not set]
Login data .......: [not set]
Signature PIN ....: forced
Key attributes ...: rsa2048 rsa2048 rsa2048
Max. PIN lengths .: 64 64 64
PIN retry counter : 3 0 3
Signature counter : 0
KDF setting ......: off
Signature key ....: [none]
Encryption key....: [none]
Authentication key: [none]
General key info..: [none]
$ gpg --change-pin # changed the PIN and Admin PIN
$ gpg --card-edit # generated the keys
$ export GNUPGHOME=/home/guru/.gnupg
$ pass init 'CCID L5'
Password store initialized for guru@unixarea.de
$ pass insert -m test
...
$ gpg --with-keygrip -K
/home/purism/.gnupg/pubring.kbx
-------------------------------
sec> rsa2048 2021-10-30 [SC]
336EB96892FE9FE7F6AD01D6529B7423F3608141
Keygrip = FCBA9E53DF1AF8D6E8D82B0418A01FA33264F704
Card serial no. = 0005 0000A6FE
uid [ultimate] Matthias Apitz (GnuPG CCID L5) <guru@unixarea.de>
ssb> rsa2048 2021-10-30 [A]
Keygrip = EE34E2B1F932D1567A6E21023F4D65B71CF953FF
ssb> rsa2048 2021-10-30 [E]
Keygrip = C544F16750F7F55DCEF781CF57C232015DDF1F90
the '>' means that these keys are on the card;
export the pub key with:
$ gpg --export --armor > ccid-L5-export-key-guru.pub
lock the card again:
$ gpgconf --reload scdaemon
I added this to the pass cmd:
$ tail -8 /usr/bin/pass
# power down the OpenPGP card
# guru@unixarea.de
#
gpgconf --reload scdaemon
sleep 2
exit 0
so the card gets loecked again after each operation with the pass cmd.
Awesome!! Thank you so much, very helpful!