@Kyle_Rankin you wrote:
“With the PureBoot Bundle, you will be able to detect firmware tampering and rootkits out of the box! Just unbox the laptop, plug in the Librem Key and turn it on–if the Librem Key blinks green, your laptop is safe; if it blinks red, it was tampered with in transit.”
“if it blinks red, it was tampered with in transit” in my understanding is the promise that what you describe in your announcement helps to detect tampering during transport.
Later on you confirm this by writing: “When you get your PureBoot Bundle, you can immediately test whether the firmware was tampered with during shipment.”
Yes, there is also the offer to contact you for a non-standard delivery: “For an additional charge, you can contact us about our anti-interdiction services which, among other measures, ships the Librem laptop and Librem Key separately.”
But how many people do understand what you write and are able to distinct between “tampering detection during shipping” and “anti-interdiction services”?
I’ll let alone the - from my point of view - nearly not detectable border between those two in your argumentation.
I looked up “interdictin” on Wikipedia and found the following paragraph:
The term interdiction is also used by the NSA when an electronics shipment is secretly intercepted by an intelligence service (domestic or foreign) for the purpose of implanting bugs before they reach their destination. According to Der Spiegel, the NSA’s TAO group is able to divert shipping deliveries to its own “secret workshops” in a method called interdiction, where agents load malware onto the electronics or install malicious hardware that can give US intelligence agencies remote access. The report also indicates that the NSA, in collaboration with the CIA and FBI, routinely and secretly intercepts shipping deliveries for laptops or other computer accessories, such as a computer monitor or keyboard cables with hidden wireless transmitters bugs built-in for eavesdropping on video and keylogging.
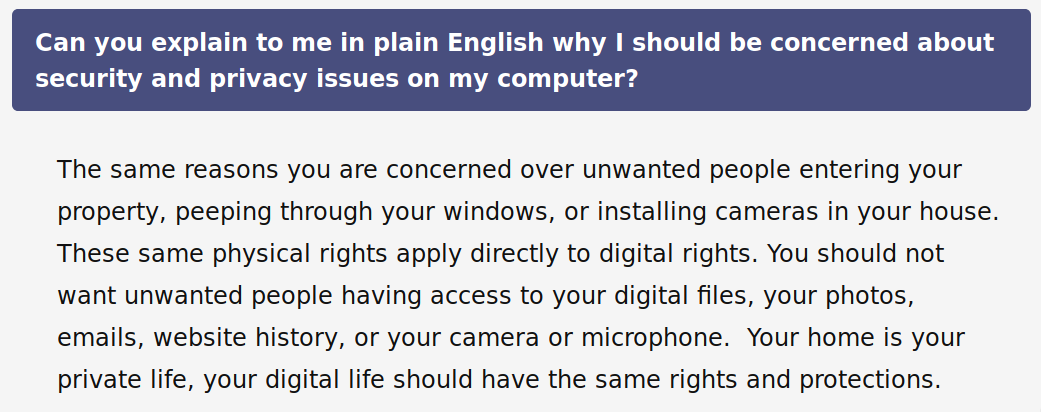
I’ll cite from your FAQ:
In your FAQ you compare security and privacy to “installing cameras” and “want unwanted people having access […] to your camera or microphone”. Theses are usually not attacks of average custom officers or script kiddies, but theses are standards you set - and for good.
From my point of view your announcement for the average user is highly misleading.
And yes, you’re right, what you call “anti-iterdiction service” has to be paid for because it needs more work and time on your side. But people are here at Purism already paying higher prices, because it is exactly what at least I want to do:
Pay a fair price (and thereby I mean that from my point of view Purisms pricing is more than fair looking at the work you put into it) to get products focused on privacy and security achieved by using open source and open hardware as far as possible - and not to forget for the necessary processes to handle this software and devices.
My suggestion: Design a way you’d like to handle secure communication for pins and passwords, calculate what it costs and what costs sending the LibremKey in an additional shipment, add it to the pricing for “PureBoot Bundle” and offer only that.