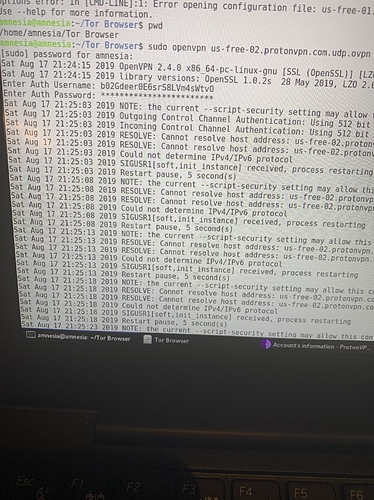
Proton VPN can be a bit difficult in setting up in Linux. Sounds like what is going on is a timing thing. First of all, you are starting the ProtonVPN before you start the Tor Browser. You should make sure the ipv6 is turned off, or ProtonVPN will not work. Secondly, I had success when using the full version of ProtonVPN, When I tried to connect to the free ProtonVPN servers in Linux, I did not have much luck. WindScribe has a free version that apparently turns off the ipv6, and then it will log on. How much do you trust security service website that is completely free? then again, after I started Windscribe service, which turned off ipv6, then I could more easily start ProtonVPN. Then I found that Mint Linux had a big button which would allow me to turn off ipv6 without all that code in the terminal. I guess I should research if Tails automatically turns off ipv6? I guess I assumed it would.
One you can ask ProtonVPN. It would attract their attention more if you had a paying account. You might try to play with a version of Linux that has a lot of users to give help. Like Ubuntu, or its spinoff-Mint Linux. I do not consider either Ubuntu or Mint Linux to be secure. But it should be easier to get help on their forum.
Then there is this:
You might want to start your own personal recipe book of what not to do, and what to do. You might notice that the Qubes OS wants the user to use two different computers. Keeping in mind that using “End to End Encryption” is the goal. One writes and encrypts a message on one computer, that is not connected to the internet. Then uses the second computer to actually log in, and send the message.
There is a website that gives advice for journalists who need to keep sources secret and so on. It is rumored that a lot of Chinese Cyber-Dissidents are in jail. I guess they trusted bad techniques. Or the government is that good. I would think the US NSA, and its other western European counter-parts would be as good as the Chinese.
Trying to prevent your ISP from knowing where you are going on the internet. Hmm. Once a tech guy at the local ISP told me that it was impossible to stop them from knowing where I went on the internet. Not sure if that was because the computer adapter I was using was a Broadcom, or some other reason Tor has some explanation of using Bridges. In fact they made it easier for us to acquire Bridges.
Someone once suggested the only way to be sure an ISP can not connect their use of the connection is to be like hiding in a grove of trees behind a public business (not on a camera) that offers Public WiFi, and an wireless adapter that can not be traced to the individual either. I guess an adapter bought with cash a long way from their usual haunts, and wait a long time after purchase before using it.
I have this vision of a Chinese Cyber-Dissident laying in the back seat of a car with a blanket over him, with his car stalled in traffic outside a place with public WiFi. He logs in, transmits his package, and his driver goes on. Perhaps the cyber dissident would climb up on top of a building close by a WiFi connection he is using. I would probably be first arrested for public trespass (or whatever the Chinese call it.)
I guess I am a bit off the original question, but it seemed relevant. I have been concerned with these same topics, and felt what I had to say might seem relevant to the OP. Then again, OP and everyone here might know a lot more about these things than I do.
https://tails.boum.org/doc/first_steps/startup_options/mac_spoofing/