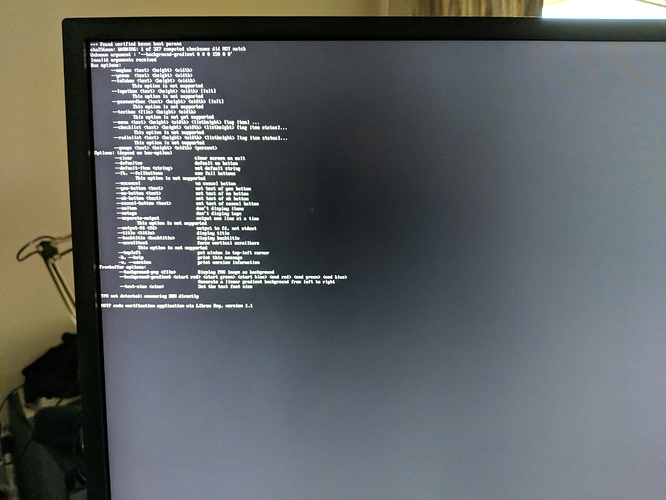
Hi,
Just received my Librem Mini. Booted it up with the Librem Key. Ran sudo apt update && sudo apt -y upgrade. Then rebooted.
Now I’m getting a brief error and then a menu. In the menu I can choose Default boot, but the same thing just happens again. What now?
I guess that’s alright after a software update.
see here
https://docs.puri.sm/PureBoot/GettingStarted.html#files-in-boot-have-been-modified
or here
How is it alright? I’m not getting any further, I’m unable to boot PureOS.
Oh, okay sorry. I thought it’s just the usual thing that you have to re-sign boot after an update. But this seems different. Maybe support should have a look.
Reading the output again I think the computed checksums message is just a warning.
It’s failing because it’s trying to display a message, but the executable is being given an option it doesn’t recognize.
Managed to get around it by re-signing the /boot files. But annoying that the dialog wasn’t showing up.
I’ll be pushing a fix for this shortly, sorry for the inconvenience
I have the same problem. But my system after trying to inspect the problem/scripts further on the recovery console now complains about signature timestamps / librem key in the future - e.g. date is 2021. currently i have not managed to use the menu to fix the issue.
If I try to sign & trust all files in /boot I get the following errors:
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
# empty line
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: no default secret key: Unusable public key
gpg: signing failed: Unusable public key
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: no default secret key: Unusable public key
gpg: signing failed: Unusable public key
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: key 9C3377ACD8ACC1E9 was created 237 days in the future (time warp or clock problem)
gpg: no default secret key: Unusable public key
gpg: signing failed: Unusable public key
/boot: Unable to sign kexec hashes
Failed to sign default config: press Enter to continue.
that’s one I haven’t seen before, but given the known issues in the current beta-12 image, I’m going to recommend everyone update to beta-13 upon release. If you’d like to test a pre-release/release candidate build, send me a PM
Currently I would need a pin for my librem key to sign my /boot again.
Can I somehow fix or re-generate the complete trust setup to have a public key that is not dated 14-Mar-2021? I suspect at the time my machine and pure os was installed the time of the hardware was 1 year ahead  … now I can either modify the time at boot or attempt to fix the script that generates the signature… a valid signature is hopefully enough, because it booted before… but perhaps the librem mini only booted before ntp corrected the clock?
… now I can either modify the time at boot or attempt to fix the script that generates the signature… a valid signature is hopefully enough, because it booted before… but perhaps the librem mini only booted before ntp corrected the clock?
I managed to recreate the gpg signature using gpg’s --ignore-time-conflict to force fix /bin/kexec-sign-config to sign my /boot:
https://www.gnupg.org/documentation/manuals/gnupg/GPG-Esoteric-Options.html
But the verification breaks as well. So I somehow need to redate my librem key? And Bios? - not sure how many copies of the public key need to be replaced.
I would recommend updating to the beta-13 test build, then performing an OEM/Factory reset from the menu to generate a new key and re-sign everything automatically
A link to the resources and instructions would help… i guess i am willing and holefully also able to do it. I just prefer not to brick the new box.
as I said, PM me, I’m not ready to publicly distribute it yet
I temporarily fixed my timestamp problem by advancing my system time via at boot:
date -s 2021 -D ‘%Y’
gui-init
But I now got a beta firmware and reset my HOTP/TOTP and re-generated a new librem GPG key.
Thanks @MrChromebox for your help and offering me the opportunity to test this.