There was a video of how to replace the private pureos encryption keys shipped with the librem 13, 14, 15 with your own privately generated encryption keys.
I wanted to see if anybody can provide the link, I can’t seem to find it on the Purism News page. In addition can this process also be used on the Librem 5?
1 Like
A process most definitely can be used on the Librem 5 - because I recently reflashed my Librem 5 and I did reencrypt i.e. for the purpose of changing the disk encryption master key. However it is likely that the process is quite different i.e. Librem 5 v. Librem laptop.
I would guess that the process on a Librem laptop would be: boot from Live Boot USB flash drive and then it just needs a sudo cryptsetup reencrypt on the correct device and partition.
By contrast, for the Librem 5, on the host computer, after download of the LUKS variant disk image and before flashing the image to the phone, you need sudo losetup ... to make the disk image file present as a loop device and then the same basic sudo cryptsetup reencrypt, again being sure to choose the correct device and partition, then sudo losetup ... to delete the loop device. (Alternatively, on the Librem 5 you can presumably use Jumpdrive in order to do the reencrypt from the host computer after flashing the LUKS variant disk image - and still exercising care to do the correct device and partition.)
Sorry, I’m not aware of a video covering this (but I am not asserting that no such video exists).
2 Likes
This worked flawlessly thank you for the tip!
Input:
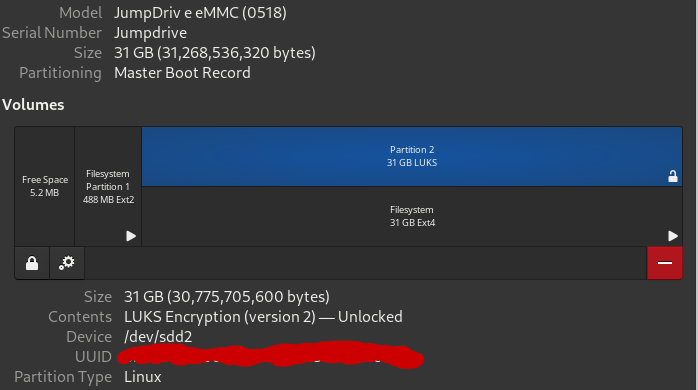
- using jumpdrive attach phone to desktop
- unlock the emmc encrypted partition using your librem 5 luks unlock password
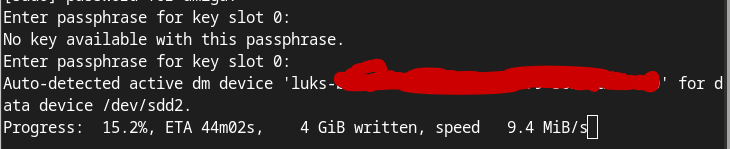
- in terminal type "sudo cryptsetup reencrypt /dev/sdd2
- in terminal enter librem 5 luks unklock password again for keyslot 0
Output:
Based on Luks:
Cryptsetup reencrypt action can be used to change reencryption
parameters which otherwise require full on-disk data change
(re-encryption). The reencrypt action reencrypts data on LUKS
device in-place.
The only question it doesn’t really say what it is doing other than re-encrypting in place. Does it generate the new master private key when it is doing that?
Never mind found it here and it should have changed the master key automatically: https://www.golinuxcloud.com/change-luks-device-master-key-cipher-linux/
You can look at the master key before and after reencryption to make sure it has changed using:
dmsetup table --target crypt --showkey /dev/mapper/secret
2 Likes
Yep.
Note that you can use cryptsetup to do the same thing i.e.
sudo cryptsetup luksDump --dump-master-key
Also, the standard caveat applies (for either command) regarding handling the master key. You must keep it secret. Therefore it is highly desirable never to output it to a file unless you are intentionally backing it up and you do so in a way that protects the file that contains the master key with the same importance as protecting the original file system.
In short, don’t add >somefile to the above luksDump command unless you know what you are doing.
Apart from generating a new random master key and then re-encrypting in order to use that new key, reencrypt could in principle be used to change other encryption parameters that relate to the encrypted disk content (as distinct from those parameters that relate to a keyslot). So let’s say that a better disk encryption algorithm comes along than aes-xts-plain64 or let’s say that advances in brute forcing mean that you need to use a longer key … then again you would have to reencrypt.
2 Likes