Details here: JMP: Frequently Asked Questions
US$4.99/month for the first line, US$2.45 for additional line in same account. Includes US$1.04 of calling credit; above that, rates are very cheap: https://jmp.chat/pricing/USD#US
… or all of them.
Details here: JMP: Frequently Asked Questions
US$4.99/month for the first line, US$2.45 for additional line in same account. Includes US$1.04 of calling credit; above that, rates are very cheap: https://jmp.chat/pricing/USD#US
… or all of them.
I suppose not, but in the interim, did anything change for WiFi calling on the L5?
I’m just getting started with this, but I can use a callcentric SIP account to make and receive calls on my L5 with wifi enabled and cellular modem disabled. Mostly experiments from my land line.
I/m also just getting started with SIP. I also bought an Analog Telephone Adapter (ATA), installed twinkle on my laptop, and played with this on my PinePhone. Audio quality is great using the ATA and a cordless “analog phone” (the cordless part is of course digital) and terrible with twinkle. I think the audio quality on the L5 and PinePhone is somewhere in between, but I haven’t actually talked to anyone else with them, unlike with the ATA and twinkle.
I only tried the dialer app on the L5 and PP, registering the account was reasonably easy.
I have only used the L5 and PP a tiny bit for anything, so I can’t really compare cell service with SIP on either and I don’t have cell service on the PP.
For the first time I set the dialer account to SIP on the L5, placed a call, hung up, and without changing anything on the L5 dialed the L5 cellular number from a land line, and the L5 rang and I was able to accept the call. Then hung up and again without changing anthing on the L5, used the land line to dial the L5 SIP number and it rang and I accepted the call.
Just did another experiment.
With L5 wifi disabled, cellular enabled, mobile data enabled, the L5 dialer will place a call over cellular even with the dialer account set to SIP as verified by caller ID and SIP carrier call history (no record of call, caller ID on incoming phone showed cellular number.
Is the ‘Use for phone calls’ toggle enabled in the preferences?
Yes. Also ‘Automatically Connect’ is enabled.
WiFi Calling may mean different things to different people but to me “WiFi Calling” means … you have a cellular account and a SIM for it but the call goes via WiFi (e.g. via your home internet) to your cellular provider and is otherwise treated as a normal cellular call.
So in essence your e.g. home internet substitutes for the cellular network. People use it when they need mobile calling but at home the mobile signal is a bit sh!t and actually using the home internet is a better option. (Conversely, if your home internet is a bit sh!t, it is a good idea to disable WiFi Calling so that your phone does not automatically failover to using the home internet when the mobile network is out.) Of course this is all academic with the Librem 5 until such time as it supports WiFi Calling within the meaning that I am using it.
A decent brakedown of the differences:
“Security” under “WiFi Calling”:
Secure when using carrier network, however, unsafe when used on public networks.
I wonder why that is. AFAIK, IPsec is used to set up a tunnel between the “customer equipment” (your phone) and some acronym soup on the provider edge. And that’s what I see when I inspect traffic on my router when my girlfriend uses this feature. Maybe it depends on the provider?
I think there is more trust on using carrier networks and their security features (and other security resources) vs. using a local wifi which may be compromised (or are mostly more easily compromised). There are several attacks types that could occur, from preventing such connection (from specific device or user even) to attacking the tunnel (in theory: creation/MITM, metadata/routing or just recording traffic for later decryption) etc. This is not to say that similar types couldn’t happen in carrier networks, but that’s whole other type of risk level. I’d imagine the carrier networks are here assumed to be at least “commercial grade” (filling all kinds of standards and requirements that national and global entities impose, noting also that 4G and 5G have brought with them better network security - if implemented) while WiFi’s could be anything. So, the one sentence assessment is a generalization. Even in your scenario the wifi setup is secure and trusted only if the social contract is upheld and you don’t have motivation to do something nefarious. Maybe a better question should be, is using wifi trusted to be secure (and private) enough - for the message/content and risk profile the users have. Properly set up IPsec should guarantee trust enough for all everyday cases.
Sorry, I was conflating WiFi Calling and VoIP. I’ll try to remember the distinction.
I don’t know the answer to your question but IPsec is challenging in the face of NAT and a typical IPv4 home network has a public IPv4 address on the WAN side but private IPv4 addresses on the LAN side, and NAT between them, or worse. So in a genuinely public setting (e.g. the prototypical “internet cafe” or “airport/hotel WiFi”), the security might be questionable.
You’re right. I had to actually refresh my memory on this a bit by looking at some old textbooks (felt very old school in this time of ubiquitous LLMs).
I’m assuming IPsec would be used in tunnel mode with ESP, where the entire original IP datagram is encapsulated (encrypted and authenticated) and a new IPv4 header is added:
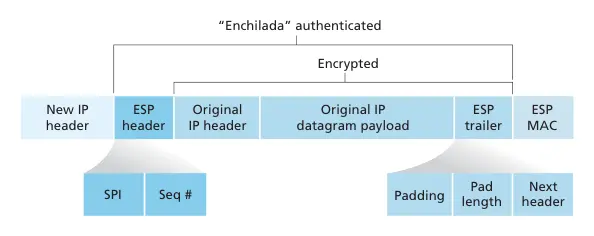
The new IPv4 header is not authenticated, which opens the door for NAT44. However, because the payload is encrypted and the transport layer information (TCP/UDP source port) is hidden, PAT is not possible. So something like NAT Traversal (NAT-T) has to be performed, where the ESP is carried inside UDP packets which do have ports that can be manipulated by NAT routers.
Initially, the source and destination ports on those UDP packets are 4500, which is exactly what I sniff in my router.
Anyway, it looks like a big mess but doable. (When is IPv6 due again? ![]() )
)
Indeed. I was going to make the same observation. IPsec was specified as part of IPv6, where it was presumably anticipated that it would never have to deal with NAT, and then, with the glacial adoption of IPv6, IPsec was retrofitted to IPv4, where NAT is commonplace. Hence the yuckiness.
I honestly don’t know. It may even differ from one carrier to another. I wouldn’t necessarily assume that. If using tunnel mode, I would think that it would have to be a split tunnel because a significant point of modern smartphones is that IP-based applications can run in the background or even in the foreground while a phone call is in progress, and ideally that wouldn’t change just because the call is via WiFi calling.
If you are sniffing on your router then maybe you can determine the answer.