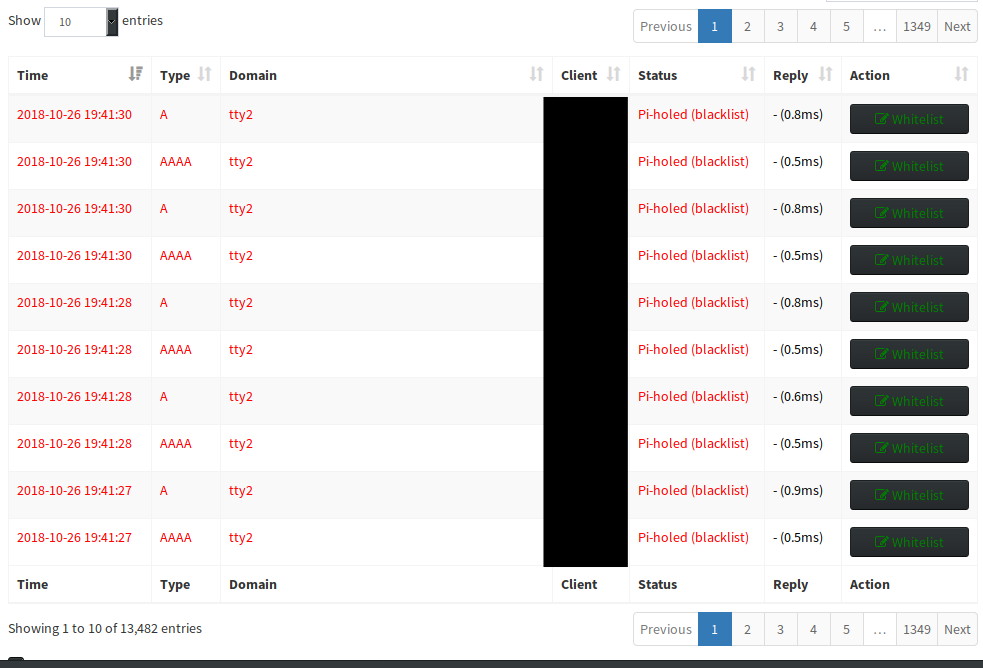
Background: I have a Pi-Hole and have been successfully running it for about 2 months now. A Pi-Hole is (as their tag line suggests) “A black hole for Internet advertisements”. It effectively redirects advertising URLs to it’s own domain and - voila! - ads disappear from devices running their DNS through the Pi-Hole. Pi-Hole (PH) users can query DNS transactions made from devices connected to the PH.
Attached is a snapshot - which will also serve as reference for my question:
As you can see, PH’s query feature enables me to see Time, Type (A=IPv4, AAAA=IPv6), Domain (i.e., hxxp://google.com, etc), Client (device named), Status, Reply, Action (enables user to instantly Blacklist the domain in the entry).
What you see in this image are entries for my PureOS Librem. In the span of ~3hrs, PureOS attempted the Domain TTY2 over 12,442 times. As a result, I’ve blacklisted this domain.
The Question: What is this TTY2 domain the PureOS is sending out so frequently and what is generating it?
Thanks for your thoughts!
-LS