@skyvine mentioned something in Driver updates on librem 5 - #5 by skyvine that stirred a thought, which kinda nags me as I briefly noted this a few years back when looking at alternative modems:
CVE (Common Vulnerabilities and Exposures) notifications specific to L5 (or any devices - in this case - Purism’s) are not listed, at least easily (as is with most devices, especially by small operators which are often on linux). This is not good in general but certainly something that should be part of a secure platform (hardware, OS and other software).
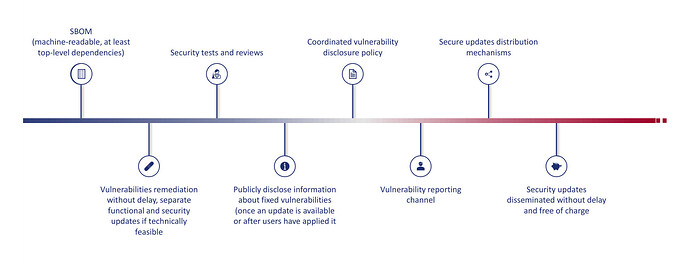
It’s not a straight forward thing to do, but not impossible either. A device has many components, which sometime hide inside them other components and sub-components and so on. So, CVEs are not always directly linked to a specific device. The hardware and software bill of materials (BOM) - which is becoming a reguirement for most things. A decent rundown on EU CRA with comparisons to US: Organizations will need to have vulnerability and incident reporting in place by Sept. 11, 2026, while other requirements (such as those related to SBOMs) will take effect on December 11, 2027. This is going to cause some work and it should be done already regardless of the CRA. I hope it’s implemented for all devices, since it would boost confidence in security and help everyone, even beyond EU (although there are caveats, like the amount of work it requires).
Something to know about CVEs and vulnerabilities is, that the CVE metrics that sometimes get posted are one thing - they are a way to help create a prioritizing, as there are vulnerabilities ranging from insignificant to catastrophic, but they are not perfect - sometimes even misleading (although newer version of metric have gotten maybe a bit better).
The CVE databases (for instance: cve.org, cvedetails.com, vulndb.com etc.) list a lot of CVEs but the devil is in the details. For instance Debian has about 7600 CVEs directly and not all are even assigned in their tracker, Ubuntu has about 42000 across all releases, of which 0 (atm) are critical and still considered a vulnerability. Of course these only list the known ones (“zero days” are not known). The linux kernel CVE list may seem scarily long too. Most (non critical) vulnerabilities need special circumstances or scenario to be an immediate thereat - often you need a few of these to line up for an attack anyway, so the chances decrease a bit. Unfortunately, it is shown and known that old vulnerabilities do not seem to disappear completely, even though patches may be created - they are not always applied. Projects are not always well maintained and patching not automatic (patches may even brake stuff).
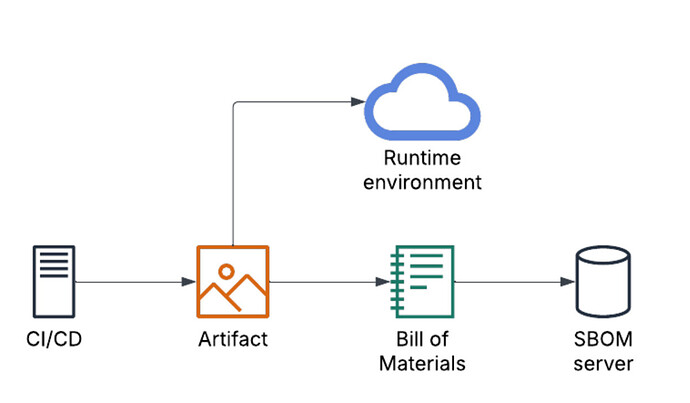
Anyways, the inconvenient though is that there should be at least a CVE tracker page for L5+PureOS components, which users could then use to determine if they can consider the device safe enough and if they (in their usecase and with their specific risk profile) can mitigate, remove or prevent the threats. Purism did have a couple of random blog posts about a few CVEs back in the day, which were informative in the sense that we knew some of the loudly talked about vulnerabilities were not a threat, but mostly they were for marketing purposes - not from s strict security and patching process. For that, a good hardware and software BOM is needed to create database searches that would list the relevant CVEs. As far as I know, that does not exist at the moment.
[Edit to add and emphasize: SBOM and CVE databases may help users but their main benefit is for the provider to keep devices secure by having an automated and systematic process that helps prioritize most dangerous vulnerabilities to fix with limited development resources - the platforms/tools seem to mostly connect to development pipelines]
There are a few “how-to” articles and projects and such related things on this, but has anyone any examples, experience of doing something like this?