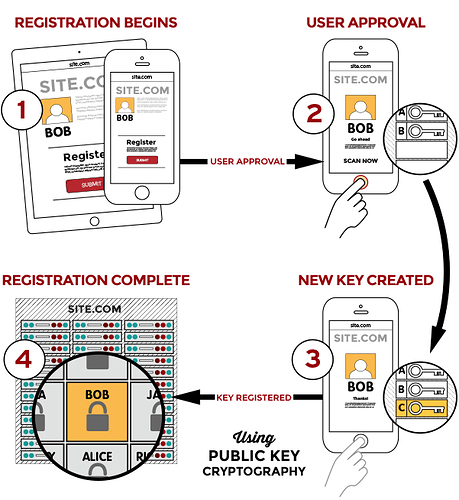
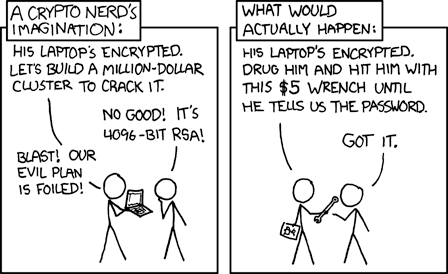
Yep I understood that. I was just generalising from “device loss” to “loss”.
… which is one reason to be down on biometrics.
However it would be wrong to think that “authoritarian government” is the only scenario where “compelled production” will occur. In the good old days of biometrics it used to be said, perhaps unreasonably, that the mafia would just cut off your finger in order to use the fingerprint to unlock something.
It isn’t obvious to me that that is true.
I can imagine that a Big Tech company like Google, who is a FIDO alliance member, if it suddenly wanted to push Passkeys, would implement it in Google Chrome (if not already) and start using its formidable internet clout and bag of underhanded tricks to get web sites to change over.
I can imagine that if I am the implementer of a new web site, I do not wish to support three authentication mechanisms
- passwords
- passkeys
- TLS client certificates
so I pick one.
If Google Chrome implements Passkeys, I as the web site implementer, having chosen Passkeys, just say to all those who refuse to use Google Chrome, well, 60% of the world uses Google Chrome, our web site is tested with and works with Google Chrome, so tough luck to you. If you want to log in then you have to submit to surveillance by the GoogleBorg.
I think it would be quite confusing for users if a web site lets them associate two or more authentication mechanisms with the same account, or the opposite, and confusing for support staff and site administrators.
For sure, that’s not going to happen overnight. In fact it isn’t really obvious what the migration strategy would be for an existing site. I expect that existing sites that have millions of users all using a password will still be using passwords for a long time to come.
Maybe. Firefox has been pushing its sync solution for a while now. I don’t know whether the keystore is within the scope of what gets synched but clearly it could be. (I personally configure so as not to allow Firefox to sync.)
In terms of backup, well, you have to do backup anyway, right? For all my “real” computers (and I include the Librem 5 in that), I just back up the entire disk. By definition that then includes the encrypted keystore - and everything else.
It’s only the iPhones where I have this OMG feeling … I have no idea what I just backed up, no idea what format it’s in, no idea whether I would be able to restore it in the future etc.